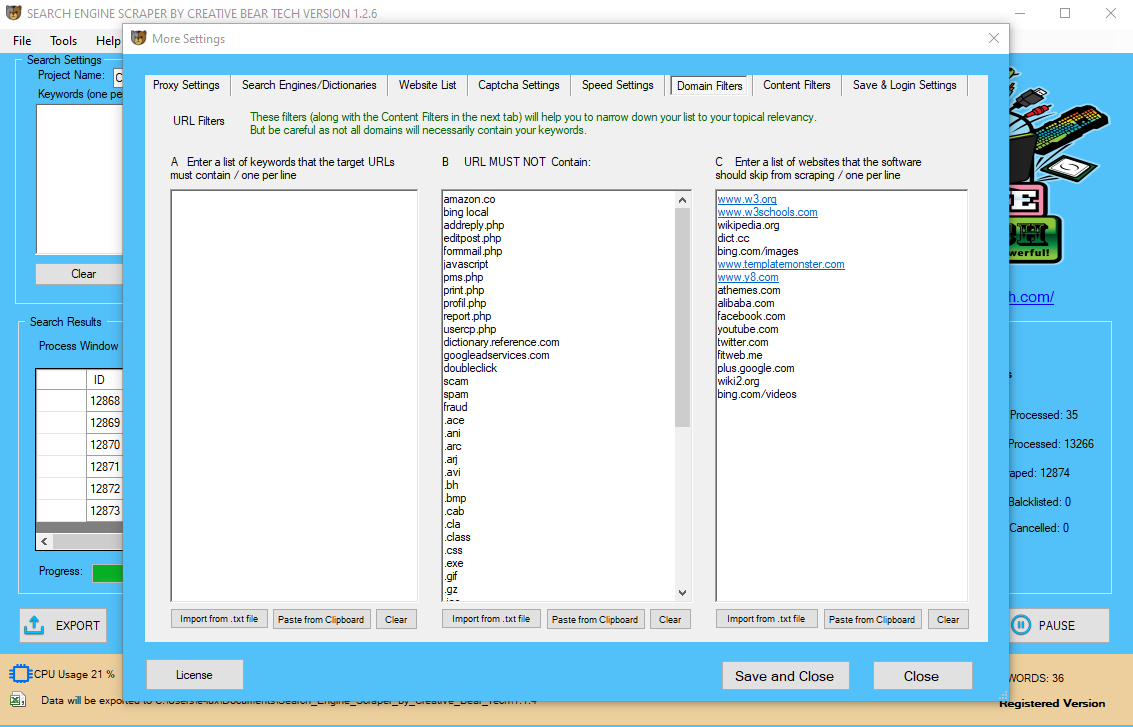
Best Data Extraction Software – 2020 Reviews & Comparison

JustCBD CBD Bath Bombs & Hemp Soap – CBD SkinCare and Beauty @JustCbd https://t.co/UvK0e9O2c9 pic.twitter.com/P9WBRC30P6
— Creative Bear Tech (@CreativeBearTec) April 27, 2020
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Another technique was used in late 2007 by the corporate iDate, which used e mail harvesting directed at subscribers to the Quechup web site to spam the victim’s friends and contacts. Web usage harvesting tracks general entry patterns and customised utilization by Web customers. By analyzing Web usage, harvesting may help to create clarity about how customers behave. This is another method to improve the perform of the Web, however on an finish-user stage. It may help designers to enhance their Web websites’ user interfaces for maximum efficiency.
Users can defend in opposition to such abuses by turning off their mail program’s option to display images, or by studying email as plain-textual content somewhat than formatted. Mozenda’s intuitive browser-based interface allows virtually anyone to be taught the fundamentals of net scraping. Users with technical know-how can even inject custom code to customize scripts, parse incoming knowledge, and manage complicated tasks by way of our strong API. Web harvesting—also known as net scraping or internet information extraction—is the method of collecting and organizing data from an internet web page. Whatever you’re gathering, the main goal of web scraping is to automate information collection tasks that might in any other case require lots of and even hundreds of labor-hours to complete.
Spammers have also harvested e mail addresses immediately from Google search results, with out actually spidering the web sites discovered within the search. Web harvesting is the process by which specialised software collects information from the Internet and locations it into files for an finish user.
A compromised computer located on a shared community phase may capture email addresses from site visitors addressed to its network neighbors. The harvested addresses are then returned to the spammer via the bot-web created by the virus. In addition, someday the addresses could also be appended with different information and cross referenced to extract monetary and personal data. For instance, attempting , , , etc. and any which might be accepted for supply by the recipient e-mail server, instead of rejected, are added to the list of theoretically valid email addresses for that area.
Web Harvesting begins by identifying and specifying as input to a pc program an inventory of URLs that define a specialised assortment or set of knowledge. Embedded hyperlinks which might be encountered may be both followed or ignored, depending on human or machine steerage. A key differentiation between Web harvesting and general purpose Web crawlers is that for Web harvesting, crawl depth might be defined and the crawls need not recursively follow URLs till all links have been exhausted.
This is a particularly interesting scraping case as a result of QVC is looking for damages for the unavailability of their web site, which QVC claims was attributable to Resultly. Web content harvesting–the process by which internet information is monitored, collected, organized and delivered–is one of the greatest tools you can utilize to make your corporation smarter. Here are examples of 5 methods net harvesting can up the ante should you’re trying to enhance your competitive intelligence efforts. With account harvesting an individual or program records login and password information from a reliable consumer to illegally achieve access to their account(s). The hacker who’s working to harvest accounts could use sniffing software to search out knowledge on a network, phishing scams, or shoulder surf to gather account info.
Putting together this discussion of social media APIs and WARCs, we’ll describe methods for harvesting social media data using existing API libraries and document the HTTP transactions in WARCs. To simplify interacting with social media APIs, developers have created API libraries. An API library is for a selected programming language and social media platform and makes it easier to work together with the API by handling authentication, rate limiting, HTTP communication, and different low-degree particulars. In flip, API libraries use other libraries such as an HTTP client for HTTP communication or an OAuth library for authentication. Examples of Python API libraries include Twarc or Tweepy for Twitter, Python Flickr API Kit for Flickr, and PyTumblr for Tumblr.
Rather than search for content, Web structure harvesting collects knowledge about the way data is organized in specific areas of the Internet. The knowledge collected supplies valuable feedback from which enhancements in areas similar to information group and retrieval could be made. In Australia, the Spam Act 2003 outlaws some forms of internet harvesting, although this only applies to e-mail addresses. One of the first major tests of display screen scraping involved American Airlines (AA), and a firm referred to as FareChase.
Library harvesting is a course of used to collect content and metadata that is obtainable without entry restriction on the open web. The deposit libraries will use automated internet crawling software program wherever possible, especially when collecting for the UK Web Archive, but can also use handbook The Best Email Tools 2020 or other strategies of downloading content material and metadata when necessary. For extra such Quality Contents on Web Scraping/Web Crawling/Data Extraction/Data Harvesting/Data Driven Services for Business, Don’t wait justGET YOUR FREE CONSULTATION NOW; content material delivery more than anticipated for positive, high quality service assured.
Spammers have additionally subscribed to discussion mailing lists for the aim of gathering the addresses of posters. The DNS and WHOIS methods require the publication of technical contact info for all Internet domains; spammers have illegally trawled these assets for email addresses. Many spammers use programs referred to as internet spiders to search out e mail handle on net pages. Usenet article message-IDs often look enough like e-mail addresses that they’re harvested as well.
Background On Social Media Apis
In basic phrases, internet harvesting is called the art of information assortment from websites, primarily for knowledge analysis. These information can be utilized for aggressive intelligence, monetary analysis, and blogging. In fact, numerous web harvesting tools have made it lots easier to pull together info on opponents and that will include financial knowledge of all types, costs, and press releases. The laws is meant to ban emails with ‘an Australian connection’ – spam originating in Australia being sent elsewhere, and spam being sent to an Australian handle. When individuals fill out a form, it’s often offered to a spammer using an online service or http submit to switch the information.
Although the cases had been by no means resolved within the Supreme Court of the United States, FareChase was ultimately shuttered by parent company Yahoo! , and Outtask was purchased Best Data Extraction Software – 2020 Reviews & Comparison by journey expense company Concur.In 2012, a startup known as 3Taps scraped categorized housing ads from Craigslist.
Massive USA B2B Database of All Industrieshttps://t.co/VsDI7X9hI1 pic.twitter.com/6isrgsxzyV
— Creative Bear Tech (@CreativeBearTec) June 16, 2020
Web harvesting software automatically extracts information from the Web and picks up the place search engines go away off, doing the work the search engine can’t. Extraction tools automate the studying, copying and pasting essential to gather info for evaluation, they usually have proved useful for pulling together information on competitors, costs and monetary knowledge of all types.
Web content harvesting entails the extraction of information by pulling information from both search web page results and from a deeper search of the content material hidden within Web pages. This additional information is often obscured from search engines like google and yahoo as a result of it is obscured by HTML code. The process scans information similar to the way in which human eyes would, discarding characters that don’t type significant phrases so as to extract helpful components. Obfuscation utilizing CSS sprites to display such knowledge as cellphone numbers or email addresses, at the cost of accessibility to display reader users.
Rather than having to re-implement all of those low-level details, ideally a social media harvester will use existing API libraries. Visual Web Ripper is a robust visual device used for automated web scraping, net harvesting and content material extraction from the online. Visual Web Ripper can routinely extract full content buildings, such as product catalogues. Your supply chain’s health instantly impacts everything from your pricing factors to your stock ranges. With a content material harvesting platform that keeps tabs on suppliers, vendors, distributors, supplies processing and the like, you’re extra prone to survive bother and capitalize on impending change.
Various web sites can easily recognize that a large number of site visitors is coming from one specific IP address and block the online harvesting from that IP address from using their website on the entire. The easiest methodology entails spammers purchasing or trading lists of email addresses from different spammers. Process of extracting data from Web pages can be referred as Web Scraping or Web Data Mining. World Wide Web, as the most important database, typically accommodates numerous information that we wish to devour for our wants.
Email harvesting is the method of acquiring lists of e-mail addresses using varied methods. Alternatively known as a web harvester, a harvester is software designed to parse giant quantities of data.
AA efficiently obtained an injunction from a Texas trial court docket, stopping FareChase from promoting software program that enables customers to compare online fares if the software program additionally searches AA’s web site. The airline argued that FareChase’s websearch software program trespassed on AA’s servers when it collected the publicly obtainable information. By June, FareChase and AA agreed to settle and the enchantment was dropped.
Canfigure is an IT Service Management solution with unimaginable flexibility. We consider in keeping it simple with easily self-deployable, price effective standalone instruments permitting you to scale up via a library of nicely designed modules, growing your number of assets and expanding you user base at a pace that fits you. With out of the field help for all IT belongings, Canfigure could be customized to hold info for any type of asset including IoT, services, transportation and more. The database schema could be extended by way of the admin capabilities with no technical information required. Asset information can include monetary knowledge and be used to track essential dates similar to warranty expiry, and linked directly to supporting contract documents.
The heart of Canfigure is a Configuration Management Database (CMDB) that underpins all other features. The CMDB holds your information within the form of Configuration Items (CIs) and the relationships between them. The National Library of Scotland and other legal deposit libraries are entitled to copy UK-published material from the internet for archiving beneath authorized deposit.
- The time period information harvesting or net scraping, has at all times been a concern for website operators, builders and data publishers.
- A current, controversial tactic, known as “e-pending”, involves the appending of e-mail addresses to direct-advertising databases.
- Data harvesting is a process to extract great amount of information from websites mechanically with the assistance of a small script.
- Direct entrepreneurs usually acquire lists of prospects from sources such as magazine subscriptions and customer lists.
- As a cheap and easy way to collect on-line information, the method can often use with out permission to steal web site data corresponding to contact lists, photographs, text e mail addresses, etc.
- By looking out the Web and different assets for e-mail addresses similar to the names and avenue addresses of their records, direct marketers can send focused spam e-mail.